The web has long been the first and most targeted attack vector in cybersecurity. It’s vast, and gives hackers plenty of choices to reach you. This is why web security measures constantly evolve to avoid and tackle threats.
Generally, developers rely on many common practices to build a safe website, such as input validation, HTTPS encryption, and more. Yet, there are still lesser-known ways that serve the same purpose. They remain effective and important to understand, especially for layered defense and resilience.
In this post, we will discuss three rare but powerful mechanisms for safeguarding your website in a scary web world.
- chroot
- Fingerprint blocking
- Content Security Policy
This is about to get technical, so be ready for it!
1- chroot, confine your application:
In Linux, chroot is an operation that creates a new root directory for a specific process. It provides an isolated environment on your machine, similar to a container.
When you chroot a process, you teach it that this current space is its /, which prevents the app from accessing system files or any other directories.
If ever hacked, the attacker will find themselves trapped in this chroot and can’t get anything elsewhere.
To visualize how it works, I created a small chroot space.
Here’s what I did:
- I made a folder /home/noha/chrootdemo/
- I copied basic Linux tools like bash and ls inside it
- I also added the required libraries for these tools to work
Then by chrooting it, I entered the room and now I’m confined, only able to see and execute what was made for me, (ls in this case)
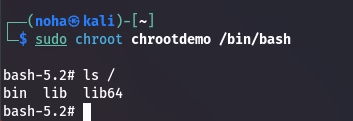
In an ideal scenario, you would want to copy all your web application files to that folder, launch your web server there, and host it with no worries.
Takeaway:
chroot doesn’t provide the security of Docker containers or virtual machines, but it serves as an essential, low-overhead layer of defense against lateral movement. It’s a key concept in the Principle of Least Privilege. Especially for a small project, static sites, or practice labs.
And while chroot gives you OS-level separation, fingerprint blocking does something entirely different…
2- Fingerprint blocking, finding that specific hacker:
Security fingerprinting is when a system collects all types of data about the attacker to identify them uniquely. This goes from browser version, screen resolution, operating system, and hardware info, even patterns of behavior like time spent on pages and click patterns.
The process goes as detailed as it can to tailor the attacker’s identity and block him through all attempts to bypass. In traditional settings, attackers use VPNs to overcome the IP block, but not with fingerprint blocking, since the device is still easily detected.
While a powerful tool, it’s also crucial to know the privacy trade-offs. The same techniques used to block attackers are applied to other users, which is why privacy browsers like Tor exist—to minimize the unique device data exposed.
Browsers, by default, expose a lot of information. With simple JavaScript code, you can be tracked and easily detected. Of course, this happens with consent by informing the user under GDPR or other privacy regulations. You can try it yourself by visiting amiunique.org or demo.fingerprint.com to check your own fingerprint and understand how websites would track and block attackers by device identity.
Like in many other areas of tech, AI is playing a huge role in fingerprint blocking as well. Trained models analyze and detect suspicious fingerprints using anomaly detection techniques. They identify patterns of bots, spoofed browsers, or other hacking signals!
This makes the website extra protected, leveling up from traditional defenses.
Ticketmaster, a ticketing platform, faced a bot assault during the 2022 Eras Tour pre-sale. In this scenario, bot farms used proxy networks to rotate through millions of IP addresses, easily bypassing traditional IP-based rate limits. Fingerprinting defeats this by analyzing the underlying machine signature and detecting the same unique fingerprint hash, despite the large number of IP addresses. This allows the platform to transition from blocking a single IP address to redlisting the originating device, the coordinator of the bot operation, instantly shutting down the attack.
Now, what about the browser itself? What if we could set a rule that protects our website from unwanted input?
3- Content Security Policy, stronger HTTP:
Code injection attacks, including XSS, are part of the OWASP top 10 attacks. Which makes them common, critical, and attention-demanding.
Simply, it is an HTTP header, a line of code that sets rules for the browser to know what to load, preventing cross-site scripting, clickjacking, and data injection.
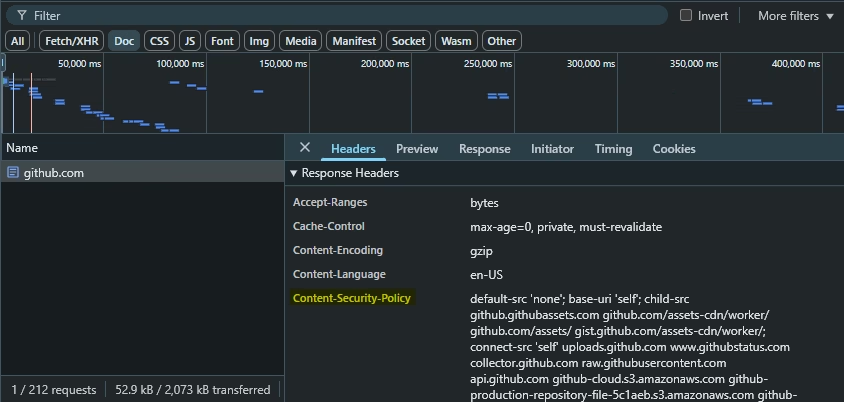
Here’s a real example of a Content Security Policy (CSP) from GitHub.com, viewed using Chrome DevTools. As you can see, GitHub blocks all content by default and explicitly allows only a few trusted sources for scripts and other resources.
To try it yourself, open your browser’s DevTools and inspect any major website. In the Network tab, under Response Headers, you find what you want.
Content security policy is often underused on real-world websites because it’s seen as extra work. As shown in the picture, it requires developers to list all trusted content sources, which many skip to avoid complexity.
CSP is often treated like a backup, a browser-level security feature that we may add if needed.
In little words
Understanding web security is essential for anyone in cybersecurity. It starts with mastering the basics and how the web works, common best practices, and reaches the rare hidden gems that may save you one day!
If you enjoyed this piece, stay close for upcoming articles! And stay safe online.